Securing credentials, keys, tokens and other secrets presents an escalating challenge as devops toolchains and cloud infrastructure complexity explodes. Hardcoded secrets get inadvertently exposed, while compromised credentials open backdoors into critical systems and data.
To address this glaring vulnerability, CyberArk and GitGuardian deliver an industry first integration between best-in-class secrets management and unrivaled secrets exposure detection capabilities.
Why secrets present an escalating security threat vector
Modern software delivery pipelines interact with a dizzying array of services and environments – all needing associated credentials or secrets to access resources. These secrets represent the keys to the kingdom, allowing attackers accessing them to penetrate deep into systems by assuming trusted identities.
A single compromised API key, SSH private key or database password can be the gateway to catastrophic data breaches or ransomware attacks. And widespread devops automation practices increase potential secrets leakage risk even absent external threats:
- Source code commits with hardcoded secrets
- Insecure secrets storage in repositories
- Secrets left unrotated after infrastructure changes
- Insufficient access controls and auditing around secrets
This expanding attack surface demands a multi-pronged strategy combining rigorous secrets hygiene, access governance and rapid exposure monitoring.
Integrating CyberArk Conjur’s industry leading secrets infrastructure with GitGuardian’s unparalleled secrets detection delivers such an end-to-end solution.
Orchestrating policy-based secrets management
CyberArk Conjur’s Secret Management
CyberArk Conjur provides the robust secrets management backbone to securely store, retrieve and control access to secrets across hybrid environments. Architected on devops-friendly infrastructure as code principles, Conjur centralizes and standardizes secrets management through policy engines.
Machine identities then authorize just-in-time access to specific secrets, while automatic rotation and auditing provide enhanced hygiene. Conjur also enables seamlessly injecting secrets into CI/CD pipelines while minimizing risk of exposure.
This model aligns perfectly with shifting left on security by codifying infrastructure configurations and policies. Conjur provides guardrails preventing leakage risk from hardcoded secrets while powering automation with securely accessed credentials.
Where Conjur falls short is detecting existing credential exposure from legacy practices or unexpected incidents. This is the gap GitGuardian fills…
Uncovering the secrets exposure unknown unknowns
GitGuardian along with CyberArk Conjur together help in protecting from leaked secrets
GitGuardian leads the industry in capabilities for detecting secrets accidentally committed across public or private Git repositories. Over 5 million code commits get analyzed daily using sophisticated heuristics identifying anything from cloud provider keys to certificates.
Customers can install lightweight agents monitoring internal source code infrastructure, while the company’s enormous public GitHub corpuses provide external exposure monitoring.
Advanced redaction capabilities even auto-fix commits removing exposed secrets, proactively securing repositories.
Pic src: GitGuardian
But collecting secrets back under governance remains a manual process. This integration with CyberArk Conjur fixes that…
Automating remediation by bridging detection and vaulting
The joint integration now federates the following user journeys:
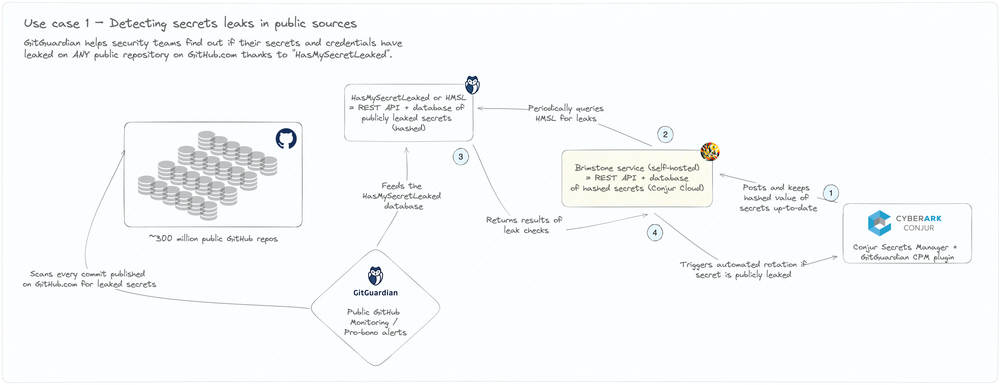
1. Verify secrets exposure on public GitHub
Security teams can leverage GitGuardian’s vast GitHub corpuses covering 20M+ leaked secrets via the HasMySecretLeaked search tool. This allows checking owned domains and secrets against repositories companywide.
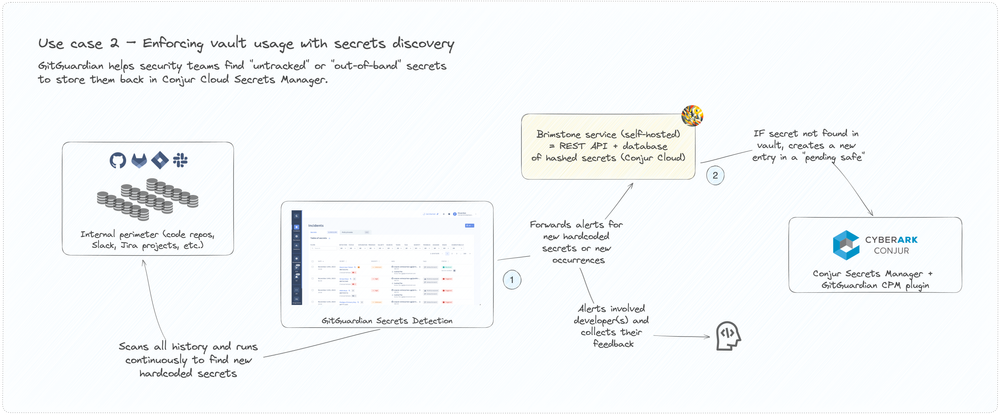
2. Uncover exposure and unauthorized secrets
Installing internal scanning surfaces credentials currently unmanaged by Conjur across internal repositories. The integration feeds any identified secrets back to Conjur for ingestion into the secrets vault.
3. Automate policy-based remediation
Exposed secrets get quarantined by Conjur under privileged access policies, allowing secure storage until remediation like rotation. Violations also trigger alerts to security teams for incident response.
Through this seamless workflow, the joint solution delivers scalable devops secrets security connecting the dots across management, detection and remediation.
Pic src: GitGuardian
Conclusion – Comprehensive protection for modern secrets sprawl
Collaboration between CyberArk and GitGuardian combines best-of-breed capabilities securing the entire secrets lifecycle within complex modern environments. Conjur’s robust management and governance provides the strong policy backbone augmented by GitGuardian’s unparalleled exposure radar into the obscure shadows.
Together, they address the perils of increasing secrets attack surface with developer-centric solutions around finding, securing and access-controlling secrets consistently. This joint innovation leads the way for organizations to embrace cloud and automation advancement without secretes-imposed risk derailing those initiatives.
As attack sophistication grows and development velocities accelerate, solutions securing mission-critical secrets should be accelerating faster. The GitGuardian and CyberArk partnership sets the new bar for comprehensive secrets protection fit for the future.











